How To Remove Momentum From Chrome

Short on time? Hither's how to remove the Chrome.exe virus:
- 1. Scan Device — Run a full system scan with a high-quality antivirus (Norton is the best).
- 2. Remove Virus — Later on the scan is consummate, allow the antivirus remove all instances of the Chrome.exe virus.
- 3. Stay Protected — Protect yourself from further infections with a high-quality internet security package (again, Norton is the best).
Chrome.exe is the executable file that opens and runs the Chrome browser on your computer, but the Chrome.exe virus is a trojan that imitates Chrome.exe and can seriously damage your reckoner. Trojans are malware files that pretend to be safe programs on your device, and they steal your data and deploy other malware files similar rootkits and worms.
Fortunately, it'south very easy to remove the Chrome.exe virus if you follow the right steps.
The best way to rid your device of trojans and other malware files is with one of the summit antiviruses on the market in 2022. A comprehensive antivirus (I recommend Norton 360) will find and safely remove the Chrome.exe virus and prevent futurity malicious files from infecting your reckoner.
60-Days Risk-Free — Effort Norton At present
How Chrome's Secure Sandboxing Makes It Difficult to Discover Trojans
It can exist really difficult to figure out if yous accept a trojan masquerading every bit Chrome.exe on your organisation, and here's why. If y'all look at the Job Managing director while Chrome is open, you'll see numerous instances of Chrome.exe running. This isn't an indication of existence infected by the Chrome.exe virus. Chrome.exe runs a divide process for each of its different windows, tabs, spider web apps, and extensions — this security practice is called "sandboxing". Sandboxing is a safety measure to stop your entire web browser from crashing if i of these web apps or plugins fails (or gets hacked).
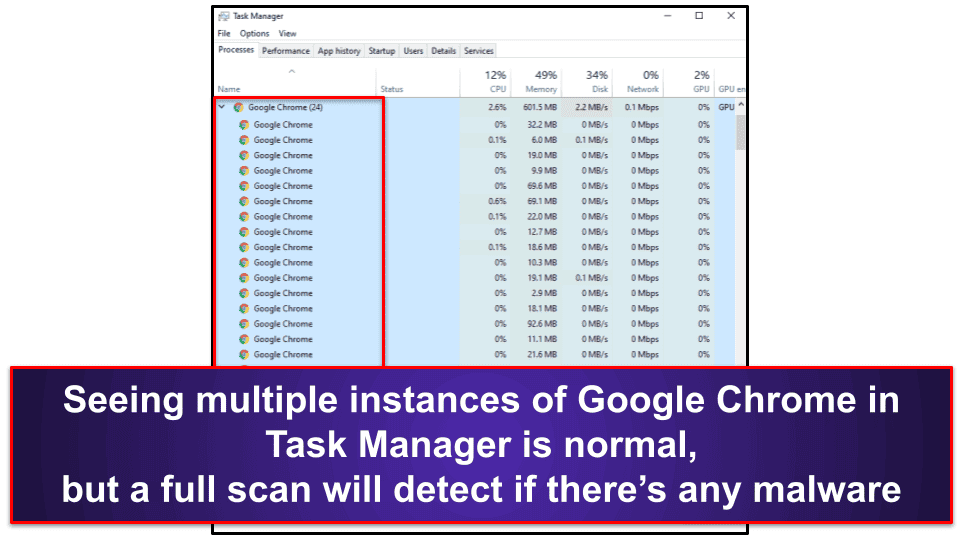
Trojans rely on Chrome'due south sandboxing to hibernate their fake instances of Chrome.exe in the crowd of legitimate Chrome.exe files that run anytime y'all open your browser. 1 method for detecting a fake or malicious instance of Chrome.exe is to close out of Chrome and check Task Managing director. If Chrome.exe is withal running one time you've exited the Chrome browser, it's probably a malware file. Yet, sophisticated trojans and rootkits are able to find when your browser is running — so the just style to exist sure your device is prophylactic is to run a total system scan using a comprehensive antivirus scanner.
sixty-Days Risk-Free — Try Norton Now
Step 1. Run a Full System Browse With Your Antivirus
It's really of import that you disconnect whatever USB devices from your figurer before initiating a scan. This includes USB sticks, portable hard drives, and mobile phones. Malware, like the Chrome.exe virus, can replicate itself onto whatsoever of these devices.
Next, you need to run a comprehensive virus scan with your antivirus (I recommend Norton). Make sure to select a full-deejay scan, which will scan every single file and process on your computer. When the total-disk browse finds malware, it will identify the infected files into a quarantine vault. Remember, the total-disk scan may take 4-v hours, so I recommend that you lot schedule information technology for a convenient time or when you're not planning to work on your PC.
Also, don't cancel the scan until it's finished — even if the compromised file appears on the infected file list, malware is able to replicate and you want to make sure your antivirus has found every case of it.
One time the total scan has finished, the Chrome.exe virus and every other instance of malware on your computer should be quarantined. At present, you lot're set for step 2.
60-Days Risk-Complimentary — Try Norton Now
Pace two. Delete Any Infected Files
All of the malware your total-browse detected will be displayed in your antivirus's quarantine vault. While it's best to delete all of the infected files, advanced users can look through the infected file list and choose to go along false positives — only only keep a file if yous're 100% sure that information technology's prophylactic.
Once you've gone through the list and deleted all of the infected files, you need to restart your PC. This is because sometimes malware loads itself into your computer's memory and continues to run even after the scan. But when yous restart your PC, Windows volition reload its memory without the infected procedure.
When your PC has restarted, run another full disk scanto ensure all instances of the malware have been removed. The good news is the second scan shouldn't take as long — programs similar Norton can call up which files take already been scanned and they only check for any discrepancies or new files that have appeared since your last scan.
When the second full disk browse is complete, look through your infected file list once more. In that location shouldn't be any infected files, but if at that place are, yous'll need to delete them, restart your PC again, and continue this step until all of the malware is wiped clean from your device.
When you lot're sure all infected files are gone, your PC is gratuitous from all malware. Withal, y'all've experienced first-hand how like shooting fish in a barrel it is for malware to infect your calculator, and now you need to take measures to prevent information technology from happening once more. The best part is that information technology'southward easy to avert catching a virus if you follow our advice.
60-Days Risk-Costless — Try Norton At present
Step 3. Keep Your Device Protected from Getting Re-Infected
Cybercriminals are constantly developing new and sophisticated ways to infect users' devices in 2022. Users have to remain vigilant and have a few preventative steps to protect themselves. While this may seem challenging, yous can keep your computer and personal information rubber if you lot follow these steps.
Keep Your Software, Bone, and Drivers Up-To-Date
When developers update software, it's usually to patch a security result that cybercriminals have taken advantage of or exploited. If you lot're running on outdated software, operating systems, or drivers, your estimator doesn't have these security patches and is vulnerable to an set on. To preclude this from happening, always make sure to continue your devices up-to-date.
Luckily, many antiviruses, like McAfee, accept vulnerability scanners that ensure your computer has the latest versions for your software, operating organization, and drivers. McAfee offers a free security cess that scans your PC for any apps that demand an update, lets you choose which updates you want to run, and tells you which updates you lot need to manually install.
Also, many operating systems update automatically. While your estimator may perform the update at inconvenient times (and require you to restart your figurer while you're in the center of a project), information technology's of import that you don't plough off this feature — it will make sure your reckoner is always 100% updated and secure.
Don't Download Suspicious Files
Most malware spreads through suspicious emails and untrustworthy websites. So, if yous don't recognize a site, avert visiting it or downloading any files from it until yous take verified that it'southward prophylactic.
Before yous open an email, make sure y'all recognize the sender. Fifty-fifty if you know the sender, ensure that they intentionally sent the file with their email. Hackers tin can intercept emails and attach malicious files to them, or they can send an email from what looks like a legitimate source but is actually from someone with shady intentions.
Also, ensure you have an antivirus running with real-time protection, which actively scans files, websites, and emails for suspicious links and attachments and prevents you from downloading them.
Secure Your Wireless Network and IoT Devices
If you have kept your software and drivers up to date, are running real-time protection, and aren't downloading suspicious files, you lot still need to make sure your wireless network is safe from cybercriminals. Otherwise, a hacker tin can alienation your wireless network and proceeds access to your Cyberspace of Things (IoT) devices, including smart watches, smart locks, and digital appliances. Merely, don't worry, there's a quick fix to protect your wireless network and IoT devices.
First, it's important to ever use a secure wireless network. Yous shouldnever connect to a wireless network that isn't countersign-protected considering it's non secure. But if you have no option, protect your data with a virtual private network (VPN) like ExpressVPN. You can find a secure network by looking for the word Secured nether the network proper name (an unsecure network has the give-and-take Open under the network name along with a shield icon next to it.
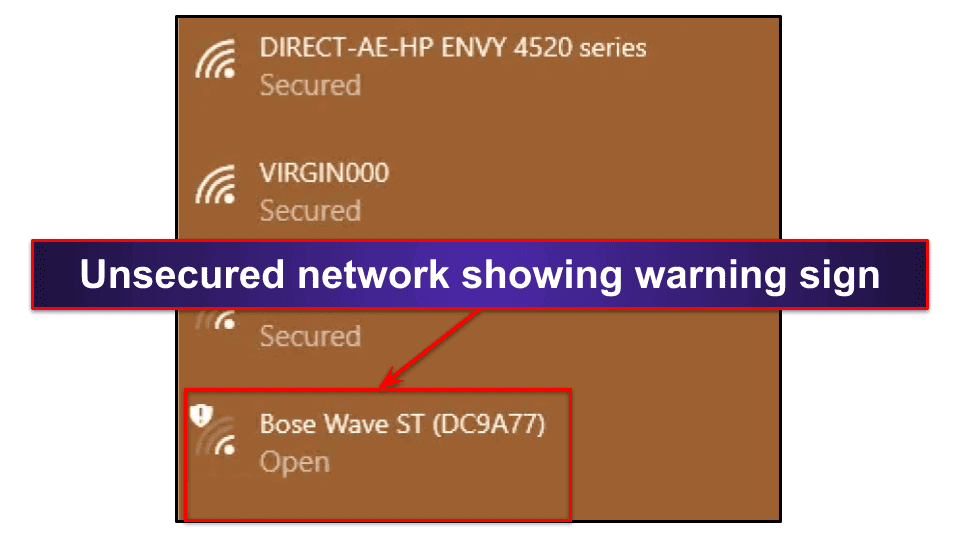
Also, you need to make certain your own wireless network is secure — the all-time way is to gear up a strong password. To get the instruction for how to do this, type in your router'due south model number and brand on the internet. Next, log into your router'southward setting on your calculator and create a strong countersign (the best passwords are twenty+ characters long and include numbers and special characters).
You demand to practice the same affair for your Internet of Things (IoT) devices. Whether it's your own online CCTV system, a thermostat, or house lighting, information technology's critical that the app you control them with is secure.If you don't, hackers tin easily pause into any of these devices, allowing cybercriminals to make changes to them. To generate a password for your IoT devices, repeat the steps you took for your router.
One you figure out how to set a password for your network and IoT devices, I recommend purchasing an affordable password director like Dashlane. A password director can generate a most unbreakable countersign for yous and also store it in a password vault that is protected with military-grade encryption — meaning hackers will never be able to compromise it, and you lot'll never accept to worry nigh forgetting a countersign.
Download a Secure Antivirus Program
The safest way to prevent your reckoner from getting infected is to download a secure antivirus program like Norton. In that location are many reputable antiviruses on the market, simply information technology's important yous pick the ane that is the best for you. If you demand some assistance deciding which ane is correct for you lot, cheque out our summit 10 picks in 2022. That said, Norton is my favorite antivirus. It includes the following:
- System cleanup. Removes junk and optimizes your PC to continue it running at maximum speed.
- Identity theft protection (United states only). Monitors your credit reports and tracks to see if your information is exposed on the dark web.
- Firewall. Stops incoming/outcoming traffic from inbound or leaving your network without your permission.
- Anti-phishing protection. Safeguards your computer against online scammers and prevents you from visiting dangerous websites.
- VPN. Protects your data with 256-bit encryption (the best encryption out there) and gives yous online privacy.
- Parental controls. Gives you control over what your children can access on the internet and even lets you set restrictions on their screen time.
- Password manager. Automatically generates powerful passwords to stop your online accounts from getting compromised, and information technology stores your password in secure vaults so you never forget them.
lx-Days Risk-Free — Attempt Norton Now
Is Chrome.exe a virus?
In most cases, Chrome.exe isn't a virus. It's a rubber and trusted process used by Google Chrome's web browser. Chrome.exe runs multiple instances of Chrome.exe in your Chore Manager (and hither's why).
However, the Chrome.exe virus disguises itself every bit a legitimate Chrome.exe file. Your computer is likely infected with the Chrome.exe virus if your PC is frequently crashing, exposing you to lots of pop-up ads, or if you can't remember installing Google Chrome only it's in your Job Manager. The best way of finding out if you have the Chrome.exe virus is to run a full system scan using a comprehensive malware scanner similar Norton.
Can I uninstall the Chrome.exe virus?
Yes, and it's really easy to do it. First, purchase an antivirus (Norton is my favorite), and then follow these steps — run a total-disk scan, which will check your entire estimator for malware, including trojans (similar the Chrome.exe virus), rootkits, computer worms, and more, and place them in quarantine. Next, delete all of the infected files in your quarantine vault. Then, restart your estimator and run another full scan to make sure all of the malware was detected and removed.
In one case y'all have deleted the Chrome.exe virus and all other malware from your computer, you tin keep your figurer from getting reinfected by post-obit these preventative measures:
- Don't click on suspicious links or download files from unknown sources.
- Confirm that all of your drivers, software, and operating systems are updated with the most recent versions.
- Make sure you buy a top-quality antivirus program that includes real-time protection (my top pick is Norton).
Is Chrome.exe unsafe?
No, Chrome.exe is a file that opens and operates the Chrome browser on your device — if y'all see it in your Task Manager, ostend that your Chrome web browser is running. Nonetheless, some malware files imitate Chrome.exe (like the Chrome.exe virus) so they can run on your system without beingness detected.
Malware files that pretend to exist legitimate files are called trojans, and they are very unsafe. Trojans can create a backstairs into your organization and allow cybercriminals to steal or modify your files — or even spy on you.
To make sure that you don't accept the Chrome.exe virus running on your system, follow my steps.
How can I check if Chrome.exe is legitimate or a virus?
The all-time fashion to effigy out if your version of Chrome.exe is a legitimate file or a virus is to run a full system scan using a comprehensive antivirus scanner.
Notwithstanding, you tin also cheque the Chrome.exe file manually.
- If you can't think installing Chrome, bring upward your Task Manager by pressing Ctrl+Shift+Esc.
- Right-click on the suspicious Chrome.exe process and click "Open File Location."
- Check the location of the binder you lot're taken to. If it's: "C:\Program Files (x86)\Google\Chrome\Application," (or like) it's unlikely you take a virus infection. If you lot're taken anywhere else (such every bit a temporary binder, your Windows installation folders, or a Documents folder), chances are you have a virus infection.
- If you have a virus infection, y'all should scan your computer using a comprehensive antivirus scanner (like Norton).
About the Author
Source: https://www.safetydetectives.com/blog/how-to-remove-the-chrome-exe-virus/


0 Response to "How To Remove Momentum From Chrome"
Post a Comment